Hey guys, welcome to yet another article of Ada Cloud Writes ✍🏾. It is a beginning of a new week and another chance to do better than last week, mistakes will always happen but let them be nothing than a stepping stone in your journey to success 🌅. I recently enrolled for my first ever hackathon as a technical writer and this is my entry to the DevCareer’s Web5 hackathon individual writing stage and I hope this article enlightens you on Web5 and its benefits over Web3.
Before I begin, I want to give a brief definition of Web5. Web5 is the next development in internet history, with the goal of giving users access to a decentralised platform and utilising artificial intelligence to integrate human emotions.
Decentralized platforms are software systems that run on a network of independent nodes with no single entity in command. They are frequently constructed on the Ethereum platform or other blockchain networks. Decentralized networks can offer more privacy, security, and freedom than major social media platforms such as Facebook, Twitter, YouTube, and Reddit4. Minds, Aether, Mastodon, Steemit, Pixelfed, Peertube, LBRY, and Diaspora are some instances of decentralized platforms.
🌫️ Evaluation of Web1 to Web5
Web 1 is the first stage of the World Wide Web's evolution. There were only a few content suppliers in Web 1, with the great majority of users being content consumers. Personal websites were common, with static pages hosted on ISP-owned web servers or free web hosting providers. It is appropriate for use as a personal website. The user is charged based on the number of pages seen. It has directories where users may search for specific information. The main goal of the websites was to make information available to anybody and to establish an online presence. Web 1's key protocols were HTTP, HTML, and URI.
Web 2 websites emphasize user-generated content, usability, and interoperability for end users all around the world. As developers of user-generated content in a virtual community, Web 2 users can connect and cooperate in social media conversation. Web 1 is an enhanced version of Web 2 that enables for more flexible web design, creative reuse, upgrades, and collaborative content creation and modification. AJAX and JavaScript frameworks, for example, are used in web 2 development. AJAX and JavaScript frameworks have recently gained popularity in the development of web 2 sites.
Web3 refers to the evolution of online usage and interaction, including the conversion of the Internet into a database. After a long period of focusing on the front-end, it allows the web's back-end to be improved. Web 3 is a term used to describe various modes of web consumption and engagement. In this instance, data is shared rather than owned, and multiple services present different views of the same site/data. This is especially important in terms of computer conceptualizations of human comprehension. The Semantic Web necessitates the use of a declarative ontological language, such as OWL, to develop domain-specific ontologies that machines may use to reason about information and reach innovative conclusions rather than simply matching keywords.
Web4 is still in the works, with no clear definition of what it will involve. Web4 is also known as the symbiotic web. The symbiotic web's dream is interaction between people and robots in symbiosis. Web4 will allow for the development of more advanced interfaces, such as mind-controlled interfaces. Although little is known about Web4 and its technologies, it is obvious that by embracing artificial intelligence, the web is progressing toward becoming an intelligent web.
Web5 is the internet's next generation, and it is predicted to change the way we communicate, access information, and conduct business online. Advanced technologies such as artificial intelligence (AI), machine learning, blockchain, and augmented reality (AR) will drive this new phase of web development. Web 5.0 will also have a more decentralized architecture, giving individuals more control over their data and online interactions.
🌫️ Web5 Overview
Web5 was recently revealed by Jack Dorsey's TBD crypto venture. According to their official website, the goal is to create an additional decentralized web that puts you in control of your data and identity. According to the official website:
“The web democratized the exchange of information, but it’s missing a key layer: identity. We struggle to secure personal data with hundreds of accounts and passwords we can’t remember. On the web today, identity and personal data have become the property of third parties. Web5 brings decentralized identity and data storage to your applications. It lets devs focus on creating delightful user experiences, while returning ownership of data and identity to individuals.”
Web5's mission is to produce a one-of-a-kind set of tools built on Bitcoin that will transform the financial system as we know it. This would allow investors and people to not only preserve and own their data, but also maintain control over all of their relationships. Developers will be able to create decentralized web apps (DWA) with verifiable credentials and decentralized web nodes using Web5. In contrast to the existing system, which relies on intermediaries to control identifiers, it focuses on decentralized identifiers that allow people to own and control their data. One of the primary differences between Web5 and Web3 platforms is that Web 3.0 platforms are typically more centralized in terms of what users think, despite marketing efforts to the contrary.
The BlockHead, one of Jack Dorsey's Bitcoin business entities, is actively developing the Web5 platform. Dorsey is a former co-founder of Twitter as well as a programmer and online entrepreneur. He recently analyzed Web3 and its limits, believing that it is owned by venture capitalists and restricted partners and is not as decentralized as it promises.
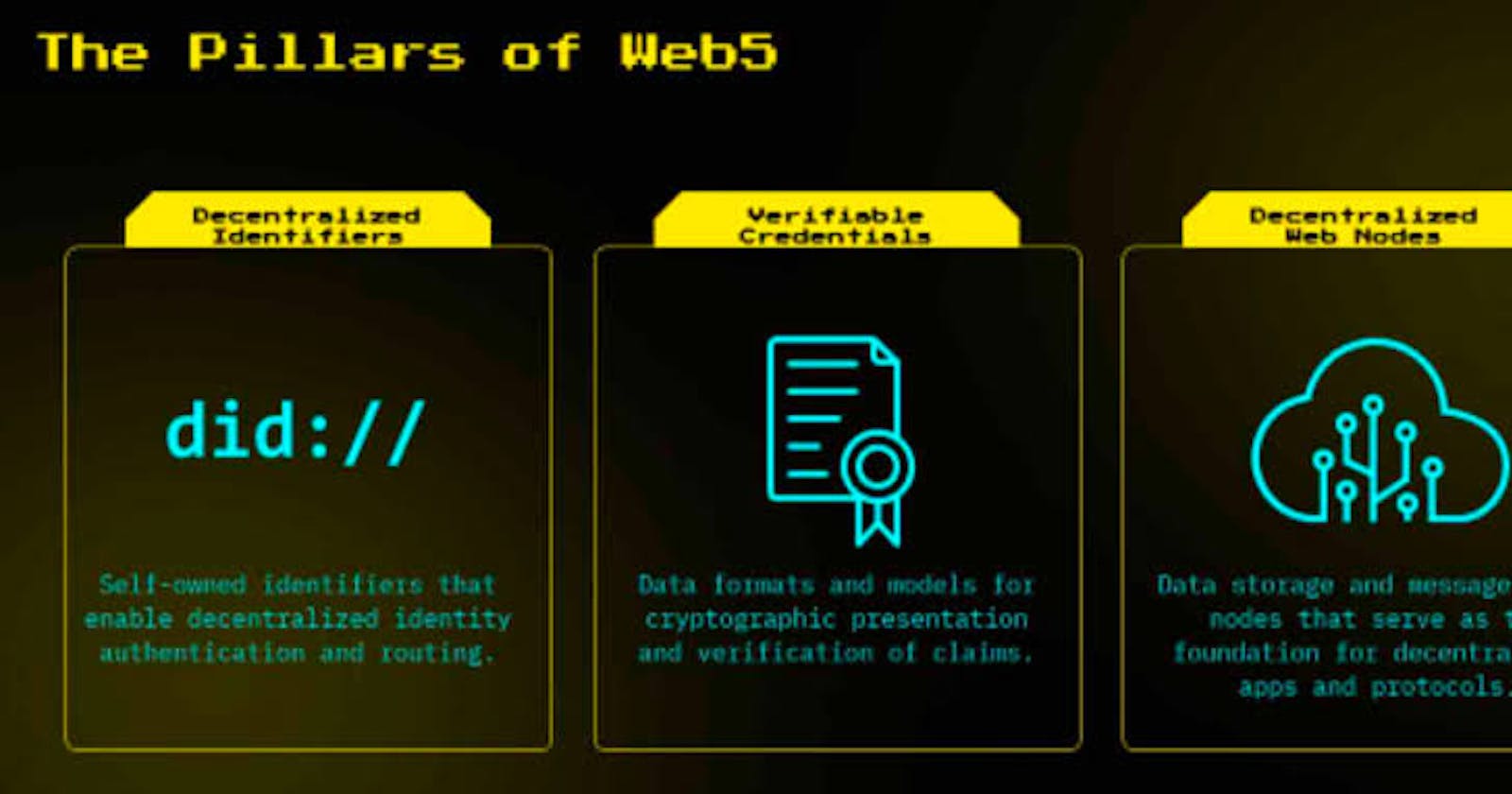
🌫️ The Pillars of Web5
Web5's pillars are the three fundamental pillars of the decentralized web platform, and they are all based on open standards.
Decentralized Identifiers: Identifiers that are owned by the user and allow for decentralized identity authentication and routing.
Verifiable Credentials: Verifiable credentials are data formats and frameworks for cryptographic presentation and claim verification.
Decentralized Web Nodes: Nodes for data storage and message relay.
Web5 additionally makes use of a self-sovereign identification service (SSIS) and an SDK for self-sovereign identity (SSI SDK). Let’s discus about these pillars in details;

🌫️ Decentralized Identifiers.
A DID is a globally unique permanent identifier that is typically established and registered cryptographically and does not require a centralized authority. DIDs are a W3C specification. They have a defined framework that basically connects to you and your data.
At the moment, we all rely on unique identifiers stored in a central database and managed by a third-party company. Decentralized IDs enable us to avoid these issues by providing people authority over their data. DIDs typically operate with blockchain or other decentralized systems to eliminate the need for identity providers, certificate authorities, or centralized registries, which we have all grown accustomed to. A decentralized identifier is made up of a unique uniform resource identification string that serves as an ID and is linked to a unique, user-controlled, self-sovereign identifier in the target system, such as the Bitcoin blockchain.
A DID's syntax is analogous to how we enter website URLs into our browsers. When visiting a website, the protocol (https://), the website (example.com), and sometimes some path or page identification (/about.html) are all present. A DID's basic format is a long string of text composed of three components, as seen below:

- URI scheme identifier: This will ALWAYS be DID for a DID. The first part of this simply signifies that we are dealing with a decentralized identification.
- Identifier for a DID method: The DID Method is the true DID protein. This is the group name to which the identification belongs. If a did were a website, the DID Method is identical to example.com. It's the section that tells you where you are and what you're talking about.
- DID method-specific identifier: This string (in computer language, a string is essentially a bunch of letters and numbers next to each other) is the exact public identity for anybody or whatever needs to be identified within the DID Method. Two DIDs with the same string can exist, but not two DIDs with the same DID Method.
Storing DIDs on ION (a Layer 2network built on top of Bitcoin) is a preferred design choice for Web 5 deployment. There are no authorities, coordinators, tokens, or other centralized bottlenecks in ION, which is a decentralized substitute for DNS for identity identifiers. DIDs are the only Web5 components that interact with a blockchain, which is generally limited to anchoring the keys/endpoints associated with the ID. For example, given the DIDs below (fictional):
A: did:hashnode:grace-ezuma
B: did:medium:grace-ezuma
As the first three letters imply, both of these DIDs are DIDs. However, one of them did so under the DID Method "hashnode" and the other under "medium." Despite the fact that they each have the same string, those strings are unique to the DID Method, so each did is distinct.
Because personal data is not saved on the blockchain, the decentralized identification functions as a URI that links the subject of the DID, such as a person, item, or company, to an off-chain DID document. DID Documents are JSON files that specify how to interact with the DID subject and are stored in decentralized storage platforms such as IPFS. They are kept in decentralized storage systems like IPFS. DIDs can only be deactivated by their owners, making them censorship-resistant. The decentralized network may theoretically process thousands of decentralized identifier operations every second. The DID Document provides information such as the DID subject's public keys, authentication and verification mechanisms, and service endpoints that refer to the subject's data locations.


🌫️ Verifiable credentials
Verifiable credentials are W3C standards that have been completely certified and function in tandem with DIDs to guarantee trustless interactions. Verifiable credentials are information that can be discovered in physical credentials such as a passport, driver's license, or bank statement. So, whereas decentralized identifiers operate as a digital stamp, allowing the authenticity of data to be reviewed, verifiable credentials contain the information that needs to be checked and validated.
For example, a customer must demonstrate that he has a bank account with XYZ bank. The bank generates a cryptographically signed Verifiable Credential, which the customer stores in their identity wallet. The credential includes the issuer; XYZ, the subject; this specific consumer, and the claims, which are the customer's account number and full name. When asked for proof of banking, the consumer shows the Verifiable Credential, which has been cryptographically signed by both the customer and his bank. This is a simple, machine-readable method for sharing credentials throughout the web. The Verifier does not know or trust the customer, but they believe XYZ bank is trustworthy, and they have effectively vouched for the consumer, thus diffusing trust.

🌫️ Decentralized web nodes
Decentralized web nodes function as a mesh-like datastore, allowing a single entity to run numerous nodes that all sync to the same state. Simply expressed, in Web5, decentralized web nodes will act as storage locations for data associated with a specified decentralized identification. It implies that we can host personal data in our own data stores. The main advantages of DWNs are security and network compatibility. It is feasible to establish an extensive web of encrypted messaging, data storage, and credential sharing by combining DIDs and DWNs.
Decentralized web nodes can be hosted on any device, whether a phone, computer, or other device. It is also possible to replicate them across several devices and clouds, with all data synchronized. However, some users are likely to prefer having others host their web nodes simply because it is more convenient. As a result, new vendors will emerge offering to host users' web nodes. The good news is that users will be able to encrypt all of their personal data on Web5, ensuring their privacy.
BlueSky, a decentralized version of Twitter, is a nice illustration of how DWNs could be used. Your tweets and relationships with BlueSky are not saved with the app. They are stored with users, which means they can share their content on any decentralized social networking platform, not just BlueSky. The blockchaindoes not house your decentralized web nodes. You can host your web nodes anywhere (phone, PC, etc.) and duplicate them between devices and clouds, with all data synchronized.
DWNs have two procedures in place to allow anyone to view, write, or delete data on your node.
Permissions: Allow someone on your node to view, write, or delete certain data records.
Procedures: Install a protocol that allows you to specify data types and authorization for a decentralized web application.
To grasp this concept, consider permissions to be active, explicit, and manual, whereas protocols are passive, syntactic, and contractual.
All communication takes place via basic JSON objects known as messages. By resolving a recipient's DID and obtaining the address of their Decentralized Web Node, Web5 creates messages and assists you in sending them to their destination. A message has the ability to install protocols, provide rights, and read, write, update, query, or delete records.

🌫️ Web5 Apps to Know
While Web5 is still in its early stages of development, some apps are already experimenting with it and its decentralized web features. Here are a few that are paving the way for a fully fledged Web5.
BLUESKY
Bluesky is a social networking software built on the AT Protocol, a federated protocol designed to make social networks more resemble open systems like email or phone numbers. Bluesky assigns a persistent DID to each user in order to create a network that is not dominated by a single stakeholder. Blueskywas founded in 2019 by Jack Dorsey with the goal of becoming a "open and decentralized standard for social media." Dorsey added that the software "could be built on top of web5". Following Elon Musk's appointment as CEO of Twitter in 2022, Bluesky saw a spike in interest and began beta testing with users in February 2023.
DAMUS
Damus is a social media software based on the Nostr protocol, which describes itself as a censorship-resistant and decentralized social network. Damus does not collect data and has no body that may restrict or censor messages, thus users have complete control over the information they share. This user ownership is further supported by the app's end-to-end message encryption and the lack of a registration form that requires identifiable information. Damus users can also use the Bitcoin Lightning Network to tip other members with Bitcoin.
ZION
Zion is a peer-governed Web5 social network in which users can post material for friends and subscribers, access content from other creators, and communicate in member-run communities. Zion gives individuals control over their data by utilizing DIDs, distributed DWNs, and the Bitcoin Lightning Network. Users are also given Zion Lightning wallets, which can send and receive Bitcoin payments without incurring fees and will ultimately support other assets such as NFTs and stablecoins.
🌫️ Conclusion
The internet was invented more than three decades ago. Numerous innovations have occurred as a result of the web, but privacy remains a source of debate. The issue of privacy is so significant that legislators have been focusing on it with rules and legislation, the most recent being the CPRA - California Privacy Right Act. Web5 appears to be the only web with real decentralized architecture. In terms of real decentralization, it addresses privacy concerns, offers users authority over data, and shifts the burden of data collection on companies, with customers having the freedom to reject.